Fellow nerds, gather round, because Apple just did a thing that hits my security-engineer dopamine receptors like a perfectly timed cache warmup. While everyone is busy doomscrolling for flashy UI candy, Apple is testing a behind-the-scenes security delivery mechanism in iOS 26.3 and macOS Tahoe 26.3 called Background Security Improvements, and it’s basically Cupertino saying: “What if security patches were more like fast, incremental hotfixes, and less like waiting for the next Big Update Boss Fight?”
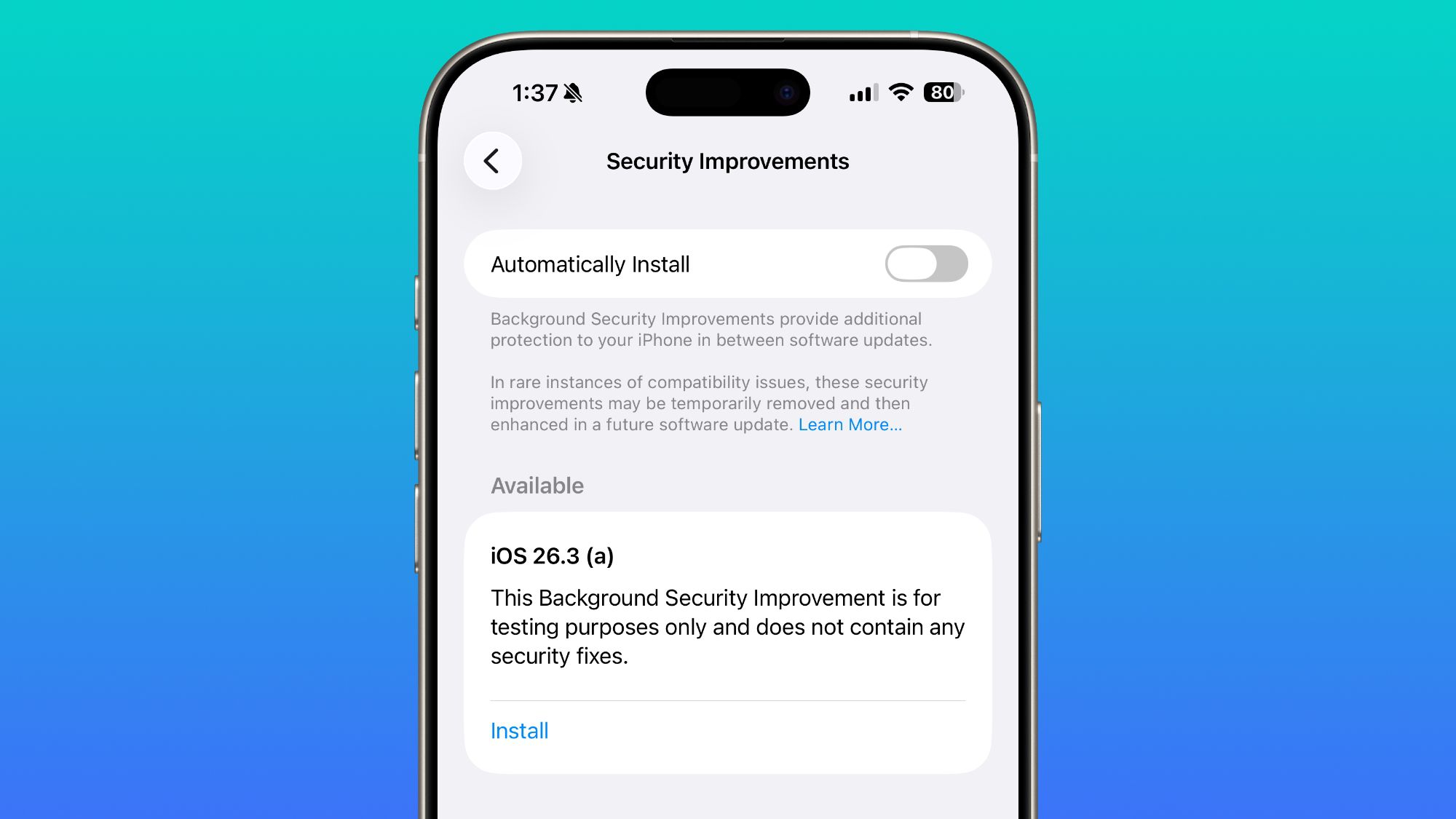
Here’s the spicy part. This is not your standard Settings, General, Software Update ritual. The test update shows up under Settings, Privacy and Security, Background Security Improvements. That location is a tell. Apple is treating this like a security posture control, not a feature release, and I love that energy. It’s the difference between shipping a new UI and shipping a new shield generator mid-battle.
According to Apple’s own description, these Background Security Improvements are meant to provide additional protections between full software updates for Safari, WebKit, and other system libraries. Translation for my fellow kernel goblins and browser sandbox enjoyers: this looks like a pipeline for delivering smaller, targeted security payloads faster, especially for the parts of the stack that get attacked constantly. Browsers are basically the modern dungeon entrance, and WebKit is a popular raid target. If Apple can patch high-risk libraries in smaller bursts, that shrinks the window between exploit disclosure and end-user protection.
Now the ultra-nerdy detail that made me do the Leo pointing meme at my screen. This particular iOS 26.3 (a) release is explicitly a test, it does not include actual security fixes. That might sound boring, but from an engineering perspective it’s huge. It means Apple is validating the distribution mechanism itself, installation flow, rollback behavior, telemetry, and device compatibility, before they start pushing real security content through it. And yes, rollback is part of the story. On iOS 26.3 beta, you can remove an installed Background Security Improvement right from that same Settings screen, which triggers a restart. That’s a very “we’re testing deployment mechanics and failure modes” vibe, and it’s exactly what you want before you trust the pipeline with real fixes.
So why should geeks care? Because if this system graduates from “beta tester toy” to “general release workhorse,” it changes the security cadence of the Apple ecosystem. Instead of waiting for iOS 26.3.1 or iOS 26.4 to get critical mitigations for WebKit or core libraries, Apple could ship smaller, more frequent background hardening updates. Think of it like a continuous delivery lane for high-impact components. Less waiting, fewer big bang updates, faster patch velocity. The dream.
Also, this fits Apple’s larger architectural obsession with compartmentalization and minimizing blast radius. If you can patch security-sensitive libraries independently, you reduce coupling to the full OS release train. That’s basically dependency decoupling, but for your pocket supercomputer. Software engineers everywhere just whispered “thank you” and did a tiny git commit in celebration.
If you’re on the iOS 26.3 beta train, go spelunking in Settings and see if the Background Security Improvements panel is available. Even if you don’t install anything, it’s worth understanding how Apple wants this to work, because this is the sort of under-the-hood evolution that eventually makes the whole platform sturdier without any marketing slides.